Setting up automatic login with SAML
General information
Advanced knowledge of SAML 2.0, single sign-on and your identity provider is required to set it up. After initializing as described here, the login can be done via the admin area of nele.ai at https://manage.nele.ai/sso To be set up, read also the appropriate manual article on the subject.
Users who automatically receive a Nele.ai account via single sign-on are not automatically deleted or deactivated. These users can manually go to https://manage.nele.ai/users be deleted.
Identity provider settings
Create a new app at Microsoft Entra ID. To do this, use the “New application” button and then “Create your own application.”
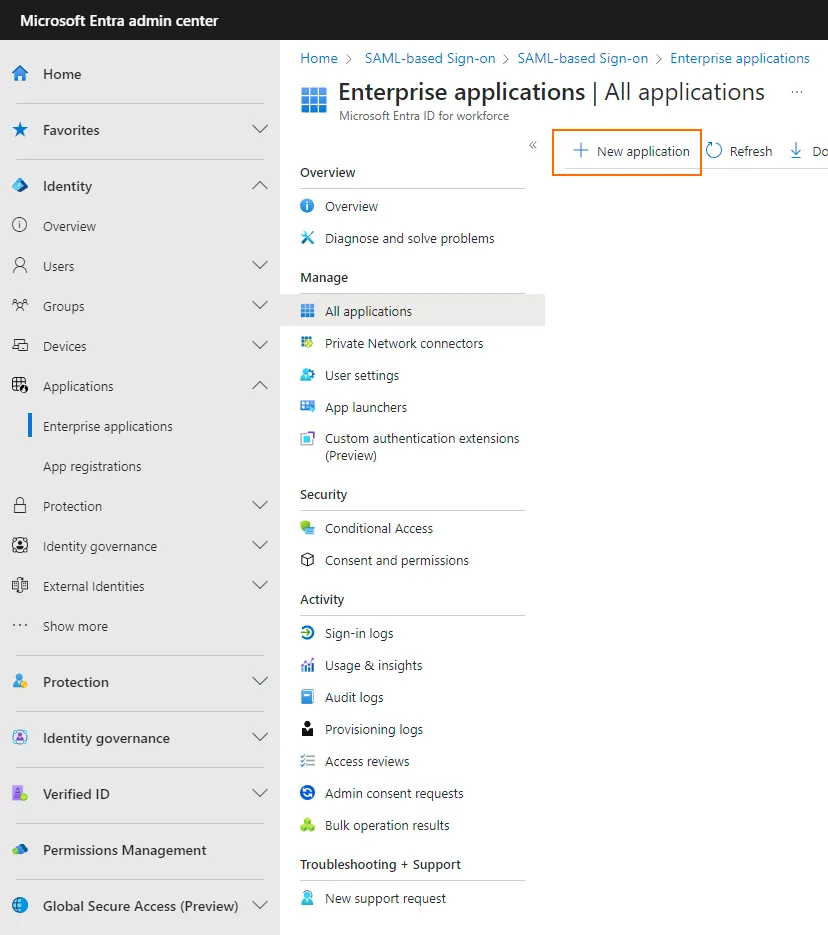
Then choose an app name and “Integrate any other application you don't find in the gallery.”
Set the single sign-on method to “SAML”.
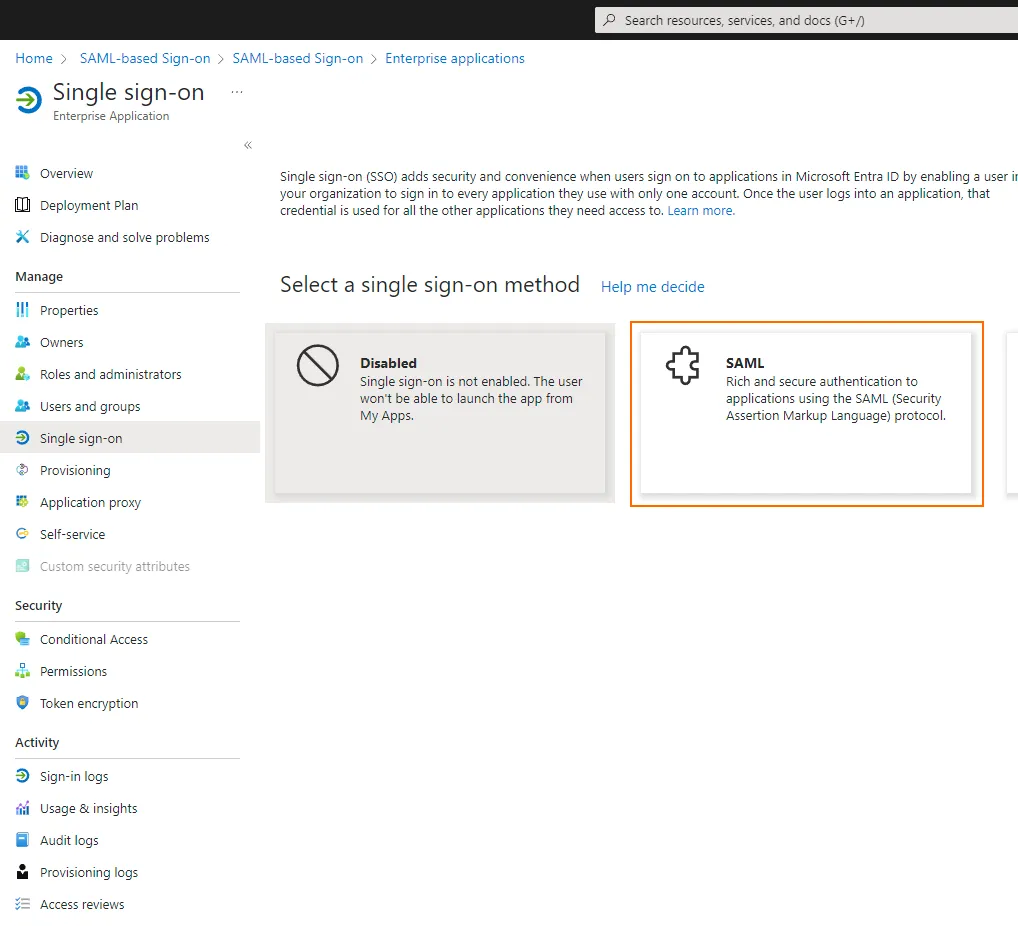
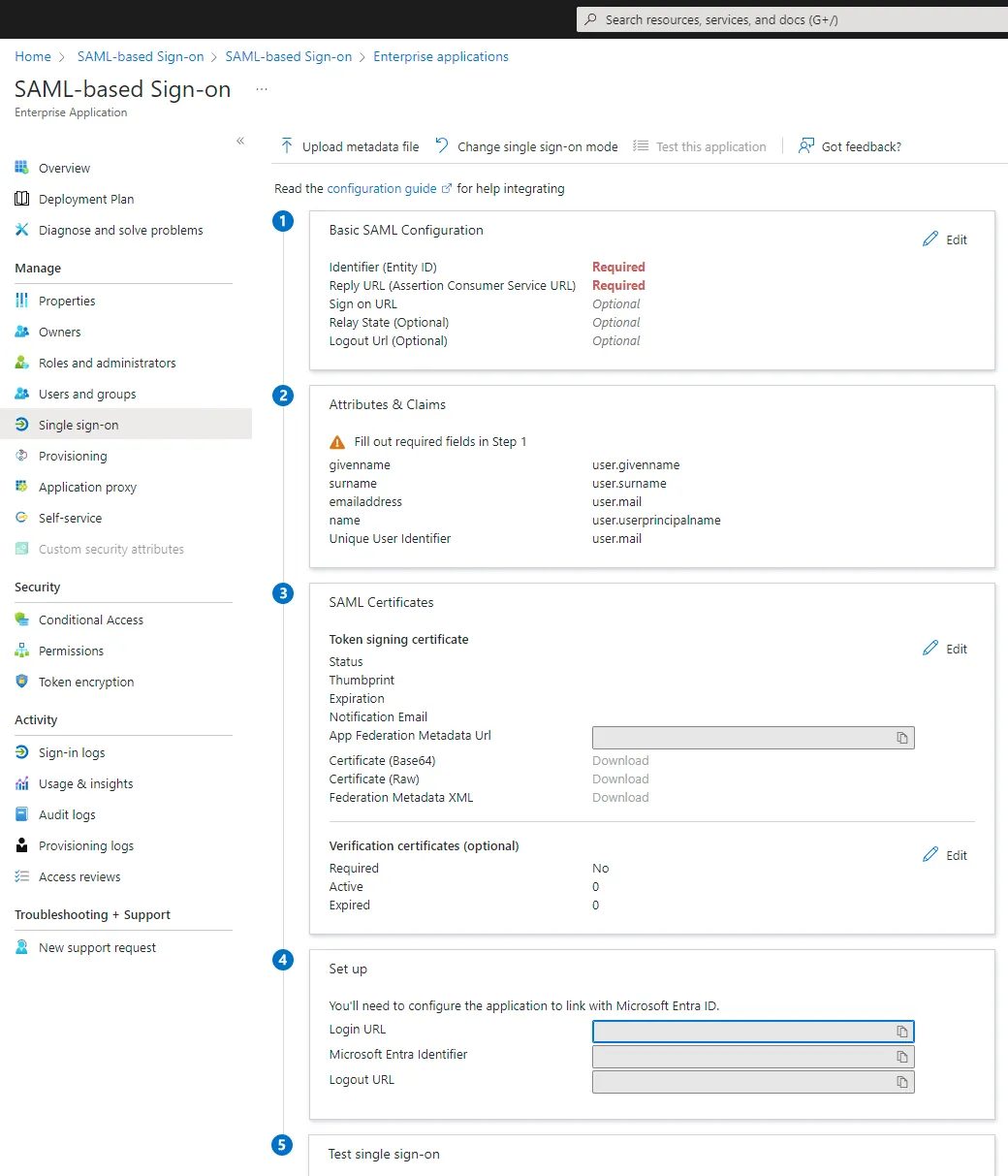
In the configuration below, first ignore steps 1 and 2, download the certificate “Certificate (Base64)” from step 3 and copy the Microsoft Entra Identifier and the login & logout URLs from step 4.
Nele.ai settings
Add the copied values to the Nele.ai settings in the admin area https://manage.nele.ai/sso one.
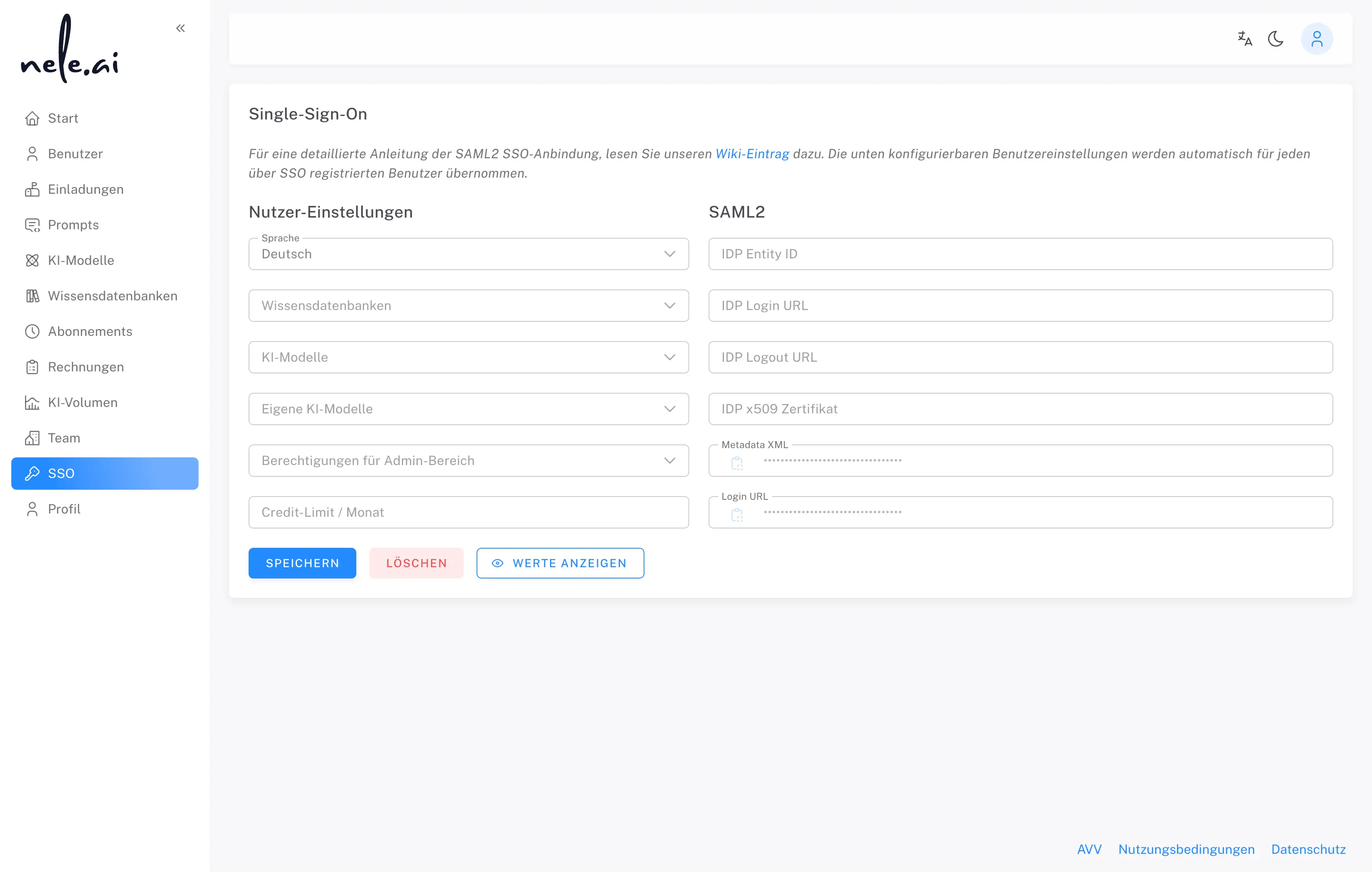
- IDP Entity ID — Microsoft Entry Identifier from step 4
- IDP login URL — login URL from step 4
- IDP logout URL — Logout URL from step 4
- IDP x509 certificate — Certificate (Base64) from step 3
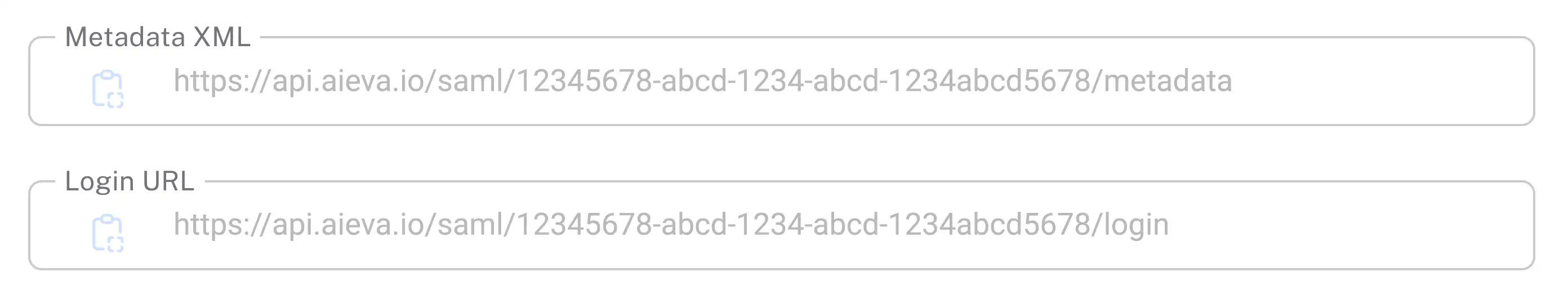
You can then save the configuration in nele.ai and open the generated metadata XML for the Entra ID configuration.
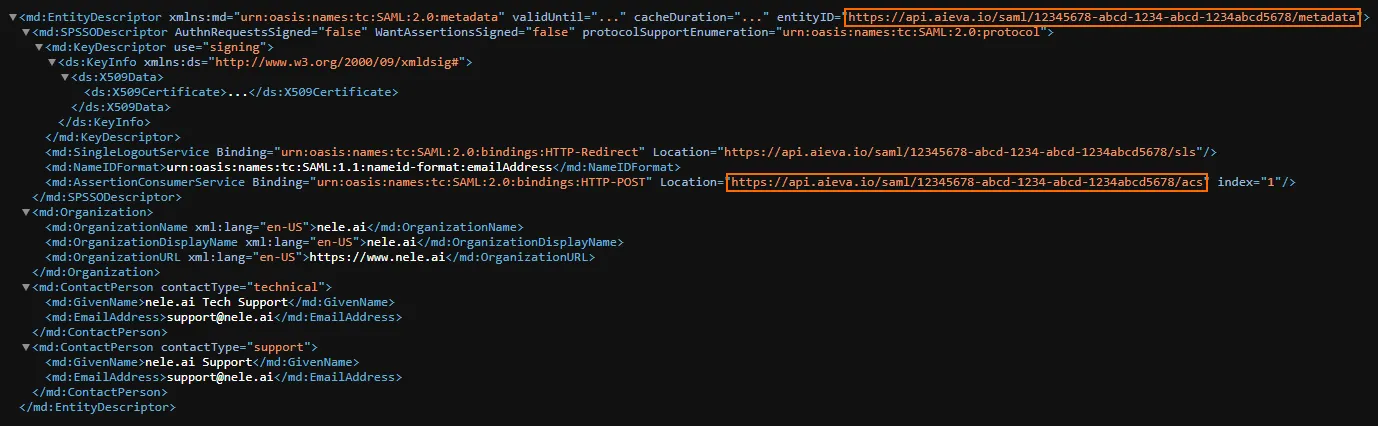
In step 1, enter the identifier (entity ID) the value entityID (URL, ends in “/metadata”) and the “reply URL” (URL, ends in “/acs”).
In step 2, set the “Unique User Identifier (Name ID)” to “user.mail [nameid-format:emailAddress]”.
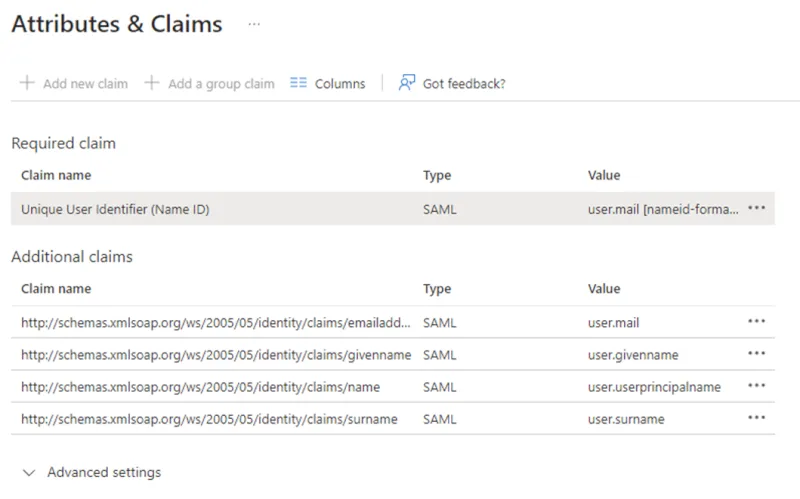
To transfer group memberships, add an additional group attribute with the name http://schemas.microsoft.com/ws/2008/06/identity/claims/groups add.
The complete attribute configuration in metadata XML looks as follows:
<md:AttributeConsumingService index="1">
<md:ServiceName xml:lang="en">
nele.ai
</md:ServiceName>
<md:ServiceDescription xml:lang="en">
nele.ai SAML service provider
</md:ServiceDescription>
<md:RequestedAttribute
Name=” http://schemas.microsoft.com/ws/2008/06/identity/claims/groups”
nameFormat="urn:oasis:names:tc:saml:2.0:attrname-format:unspecified”
isRequired="false”
/>
</md:AttributeConsumingService>
You can test a successful configuration via a link in the administration area. If everything is set up correctly, you will be redirected to an overview page where you can choose, among other things, whether you want to log in to the desktop app or the web app. Alternatively, you can download nele.ai for various operating systems there.